Industry News
5 Best Practices to Prevent Insider Threats in 2019

Data breaches caused by insiders cost enterprises millions of dollars. According to the Ponemon Institute, every year, companies lose up to $8.7 million due to insider threats. To ensure an appropriate level of enterprise data protection, security officers continuously look for ways to improve their current insider threat management solution. With the following insider threat management best practices, you’ll be able to protect your sensitive business information and keep malicious insiders at bay.
1. Consider access controls
It’s essential to keep your critical assets inaccessible for malicious insiders. First and foremost, deploy multi-factor authentication (MFA) for the most valuable systems, applications, and services. Your goal is to make sure that any malicious insider won’t be able to borrow a password from their colleagues and get a hold of the data they aren’t supposed to have access to. Therefore, you need to look for an insider threat management solution with a built-in MFA functionality.
By implementing MFA, you can make sure that the person attempting to enter the protected perimeter are who they claim to be. At the same time, the use of MFA makes it way harder for malicious insiders to access your company’s sensitive information.
It’s also important to have a good password management policy in place. The most basic recommendations include forbidding the use of default and simple passwords and changing passwords upon certain events (say, employee resignation) or after some periods of time (say, every month or every quarter).
2. Limit access whenever possible
Once you managed to make sure that only the right people can get access to your network and critical assets within it, it’s time to think about the access permissions each of your company’s employees has. It’s best to take some technical measures to mitigate insider threats and deploy the so-called least privilege principle when employees only have the exact access level they need to do their job.
But today, more and more companies go even further and deploy a zero trust security model. In a zero trust network, there’s no general protected perimeter that distinguishes trusted insiders from untrusted outsiders. Instead, each critical asset or system is fully protected from both insiders and outsiders, thus mitigating internal and external threats to cyber security.
Such an approach works best for the companies that cooperate actively with third-party vendors and subcontractors. It’s also a great solution for the enterprises with a bring your own device (BYOD) policy in place, allowing their employees to use personal devices for work purposes.
3. Monitor employee activity
User activity monitoring is the basis of many insider threat protection techniques. You need to be able to see what’s going on within your network, in real-time at best. When choosing among the solutions to protect against insider threats in cybersecurity, pick the one that allows to see a particular user session and terminate it if necessary.
Many companies also look towards User and entity behavior analytics (UEBA) as the key to effective threat monitoring and protection against insider threats. Advances in machine learning technologies allow building user profiles that include normal baseline behavior patterns for particular users or roles. Registering activities that deviate from these patterns may help detect malicious insiders and mitigate possible threats at an early stage.
4. Analyze logs and respond to security incidents
Continuous user activity monitoring is meant to give you full visibility across the enterprise network and provide you with detailed data for further analysis. Depending on the user monitoring solution, user activity logs may contain different types of information:
Names of files and applications opened by the user:
- URLs to the visited websites;
- Logged keystrokes;
- Recorded sessions, and more.
The proactive incident response also plays a significant part in building an effective insider threat cyber security program. There’s no point in detecting a malicious action if you’re unable to respond to it properly and, therefore, prevent a data breach from happening.
Look for an insider threat prevention solution that allows you both receiving real-time notifications about the detected security incidents and automating responses to the most common types of incidents. For instance, if the system registers, say, three unsuccessful login attempts, the account a user tried to access will be blocked.
Finally, if you want to be able to analyze all of the logged information on a deeper level, make sure that your insider threat prevention solution supports forensic data export.
5. Pay special attention to third-parties
Remote access control and protection is an essential part of the modern insider threat management program. Today, more and more organizations hire remote employees and grant access to critical corporate resources to third-party vendors and contractors. But, as reported in a 2018 study by the Ponemon Institute, third-party vendors were the cause of nearly 60 percent data breaches.
If granting third-party vendors access to business-critical data, systems, and application is a common practice for your organization, make sure you have an appropriate third-party management solution in place. Leverage all of the above-mentioned tools and practices to protect your corporate data from unauthorized access and use.
If your third-party subcontractors are using a shared account for accessing your corporate network or business applications, it’s preferable to add secondary authorization as an additional protection layer. This way, you’ll be able to clearly associate each session initiated under the shared account with a particular user.
And, finally, make sure that your third-parties are well aware of your organization’s cybersecurity policy and know what cybersecurity rules they must follow.
Conclusion
Insider threats have one of the biggest impacts on enterprise cybersecurity. In order to mitigate the risks related to insider threats, organizations should deploy complex solutions that include monitoring and audit of user activity, granular access and privilege management, and effective incident response.
This article is a contribution from Marcell Gogan. Marcell is a specialist within digital security solutions, business design and development, virtualization and cloud computing, R&D projects, establishment and management of software research direction – working with Ekran System. He also loves writing about data management and cybersecurity.
-

 eSports6 hours ago
eSports6 hours agoTEAM VITALITY AND PARIS SAINT-GERMAIN ESPORTS ANNOUNCE EA FC COLLABORATION
-

 Asia7 days ago
Asia7 days agoTesla to showcase Model Y with NODWIN Gaming at the thrilling BGMS Season 4 Grand Finals
-

 Compliance Updates7 days ago
Compliance Updates7 days agoSOFTSWISS Compliance Expert Shares Knowledge on AML in iGaming for Sumsub Academy
-

 Africa7 days ago
Africa7 days agoRacing1 is exhibiting for the first time at the Grand Prix D’Afrique
-

 Latest News7 days ago
Latest News7 days agoÅland-Based Gaming Company Paf Becomes Main Partner of the Finnish Ski Association – One of the Most Significant Sponsorship Agreements in the Association’s History
-

 Latest News7 days ago
Latest News7 days agoAnimo Studios debuts virtual hosts for live table games starting with Stake
-
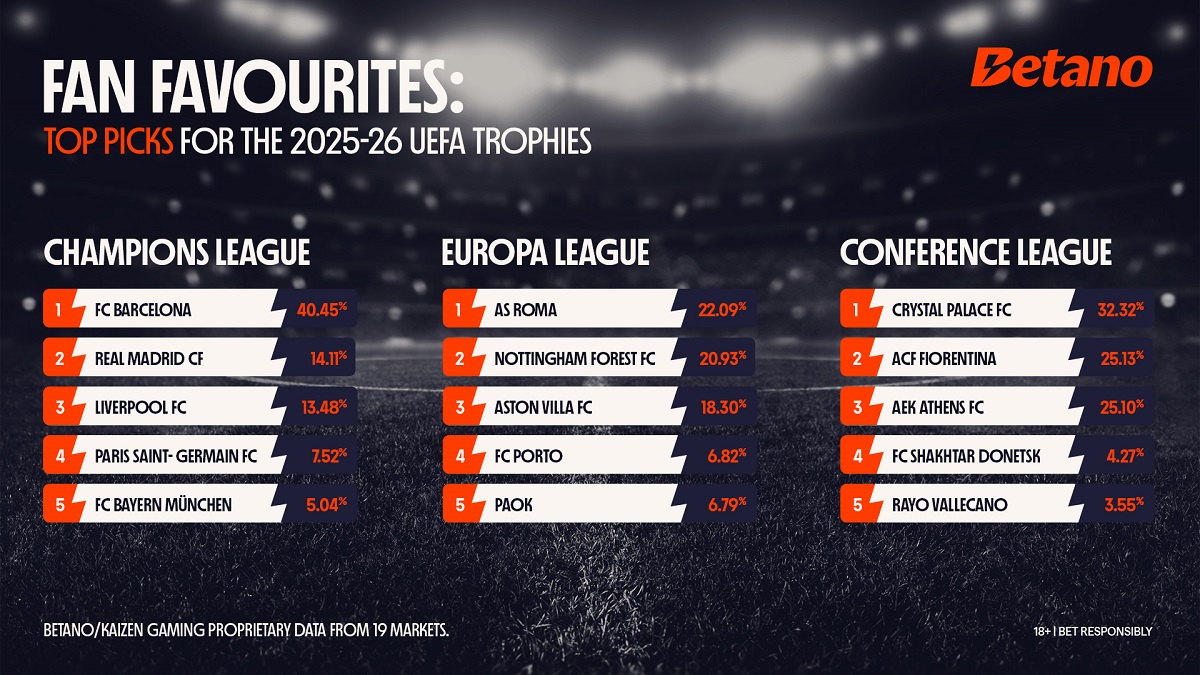
 Latest News7 days ago
Latest News7 days agoKaizen Gaming data – FC Barcelona the fan favourite to win the Champions League
-

 Latest News7 days ago
Latest News7 days agoWeek 37/2025 slot games releases